
When you think of the Microsoft SC-100 Microsoft Cybersecurity Architect exam, you immediately think about how to prepare for the Microsoft SC-100 exam. Microsoft-Technet helps you.
Below, we’ll share some useful information about the SC-100 exam, how to study for it, and some free practice resources.
Changes to the SC-100 exam
First of all, let’s start with the changes in the exam, after all, to study for an exam, you need to understand its changes first.
The exam was launched on April 7, 2022
Significant changes will be implemented from May 5, 2023
Change November 3, 2023
Change January 24, 20224
Coming soon
Updated April 23, 2024!
You’ll need to focus on the upcoming update at the end of April, which means you’ll need to hurry up and study for the Microsoft Cybersecurity Architect SC-100 exam to pass it as soon as possible.
Study for the SC-100 exam
How do you study for the SC-100 exam?
It is recommended to take a Three-step approach.
The first step is to understand the exam
| Be clear about why you are taking the exam: | Advance your career and open up new opportunities in the field of cybersecurity. |
| Be clear about the prerequisites for the exam: | To take and prepare for the SC-100 exam, one of the following three prerequisite exams needs to be completed before taking the SC-100 exam: SC-200, SC-300, AZ-500 |
| Familiarize yourself with the format of the exam: | The SC-100 exam is a wide-ranging exam and is not an in-depth security exam. The Microsoft SC-100 exam is a multiple-choice exam with 40-60 questions. The duration of the exam is 120 minutes (2 hours) and the passing score is 700 out of 1000. Exams can be taken online, at a testing center, or onsite. You need to register and pay the exam fee to schedule your exam. |
| Know the weighting of the exam area: | Design solutions that align with security best practices and priorities (20–25%)、Design security operations, identity, and compliance capabilities (30–35%)、Design security solutions for infrastructure (20–25%)、Design Security solutions for applications and data (20–25%) |
| What you can gain after passing the exam: | Passing the exam will give you the skills to plan and implement a cybersecurity strategy, design a zero-trust strategy, evaluate your security strategy, and recommend security solutions and practices. And the ability to work with other IT staff to ensure IT security by monitoring activity and applying some security policies. |
| Study resources available for studying for the Microsoft SC-100 exam | Official Microsoft study guides, online training courses, practice tests, and learning communities like forums and study groups. |
Terms related to the SC-100 exam (Popular)
- Access Control
- Authentication
- Authorization
- Confidentiality
- Cybersecurity
- Defense-in-Depth
- Incident Response
- Intrusion Detection System (IDS)
- Malware
- Risk Management
- Security Management
- Threat Intelligence
- Vulnerability
… More are welcome to be added.
The second step is to find learning resources
What resources are available to study for the Microsoft SC-100 exam? There are many, and here are the most useful ones.
To study for the SC-100 exam for you, I have put together great resources for everyone.
Book
Official
Microsoft Exam page: https://docs.microsoft.com/en-us/learn/certifications/exams/sc-100
Microsoft Online Courses: https://docs.microsoft.com/en-us/learn/certifications/sc-100
Microsoft Official mock test: https://www.measureup.com/sc-100-microsoft-security-compliance-and-identity-fundamentals.html
Microsoft Docs: https://docs.microsoft.com/en-us/security/
Microsoft Hands-on Lab: https://www.microsoft.com/handsonlabs/selfpacedlabs
Microsoft Security Community: https://techcommunity.microsoft.com/t5/security-compliance-and-identity/bd-p/SecurityComplianceandIdentity
SC-100 exam latest practice test questions
Practice tests are important for studying for exams, and taking practice tests can help you understand the SC-100 exam topics and question types.
| Pass4itSure SC-100 dumps (Total 180 Q&As) | Q&A 1-15 | Free | With detailed analysis |
Question 1:
Your company has an office in Seattle.
The company has two Azure virtual machine scale sets hosted on different virtual networks.
The company plans to contract developers in India.
You need to recommend a solution to provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements:
1. Prevent exposing the public IP addresses of the virtual machines.
2. Provide the ability to connect without using a VPN.
3. Minimize costs.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Create a hub and spoke network by using virtual network peering.
B. Deploy Azure Bastion to each virtual network.
C. Enable just-in-time VM access on the virtual machines.
D. Create NAT rules and network rules in Azure Firewall.
E. Deploy Azure Bastion to one virtual network.
Correct Answer: AE
Azure Bastion is a fully managed service that provides more secure and seamless Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH) access to virtual machines (VMs) without any exposure through public IP addresses.
Provision the service directly in your local or peered virtual network to get support for all the VMs within it.
Connect to your virtual machines in your local and peered virtual networks over SSL, port 443, directly in the Azure portal.
Azure Bastion and VNet peering can be used together. When VNet peering is configured, you don\’t have to deploy Azure Bastion in each peered VNet. This means if you have an Azure Bastion host configured in one virtual network (VNet), it
can be used to connect to VMs deployed in a peered VNet without deploying an additional bastion host.
Architecture
When VNet peering is configured, Azure Bastion can be deployed in hub-and-spoke or full-mesh topologies.
Reference:
https://learn.microsoft.com/en-us/azure/bastion/vnet-peering
https://azure.microsoft.com/en-us/products/azure-bastion/#features
Question 2:
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)
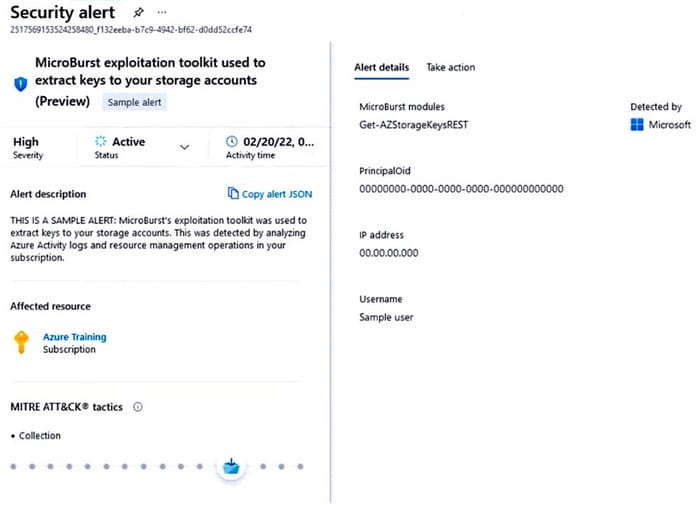
After remediating the threat which policy definition should you assign to prevent the threat from reoccurring?
A. Storage account public access should be disallowed
B. Azure Key Vault Managed HSM should have purge protection enabled
C. Storage accounts should prevent shared key access
D. Storage account keys should not be expired
Correct Answer: A
Anonymous public read access to containers and blobs in Azure Storage is a convenient way to share data, but may also present a security risk. It\’s important to manage anonymous access judiciously and to understand how to evaluate anonymous access to your data. Operational complexity, human error, or malicious attack against data that is publicly accessible can result in costly data breaches. Microsoft recommends that you enable anonymous access only when necessary for your application scenario.
Note: Attackers have been crawling for public containers using tools such as MicroBurst.
Exploiting Anonymous Blob Access Now, there are thousands of articles explaining how this can be abused and how to search for insecure storage in Azure. One of the easiest ways is to use MicroBurst, provide the storage account name to search for, and it’ll check if the containers exist based on a wordlist saved in the Misc/permutations.txt
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/anonymous-read-access-prevent https://hackingthe.cloud/azure/anonymous-blob-access/
Question 3:
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
A. Azure Key Vault
B. GitHub Advanced Security
C. Application Insights in Azure Monitor
D. Azure DevTest Labs
Correct Answer: B
Requirements. Application Development Requirements
Fabrikam identifies the following requirements for application development:
*All the application code must be stored in GitHub Enterprise.
*All application code changes must be scanned for security vulnerabilities, including application code or configuration files that contain secrets in clear text. Scanning must be done at the time the code is pushed to a repository.
A GitHub Advanced Security license provides the following additional features:
Code scanning – Search for potential security vulnerabilities and coding errors in your code.
Secret scanning – Detect secrets, for example, keys and tokens, that have been checked into the repository. If push protection is enabled, also detects secrets when they are pushed to your repository.
Dependency review – Show the full impact of changes to dependencies and see details of any vulnerable versions before you merge a pull request.
Security overview – Review the security configuration and alerts for an organization and identify the repositories at greatest risk.
Incorrect:
Not C:
Scenario: Azure DevTest labs will be used by developers for testing.
Azure DevTest Labs is a service for easily creating, using, and managing infrastructure-as-a-service (IaaS) virtual machines (VMs) and platform-as-a-service (PaaS) environments in labs. Labs offer preconfigured bases and artifacts for
creating VMs, and Azure Resource Manager (ARM) templates for creating environments like Azure Web Apps or SharePoint farms.
Lab owners can create preconfigured VMs that have the tools and software lab users need. Lab users can claim preconfigured VMs, or create and configure their VMs and environments. Lab policies and other methods track and control lab usage and costs.
Question 4:
DRAG DROP
Your company wants to optimize ransomware incident investigations.
You need to recommend a plan to investigate ransomware incidents based on the Microsoft Detection and Response Team (DART) approach.
Which three actions should you recommend performing in sequence in the plan? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:

Step 1: Assess the current situation and identify the scope.
The DART approach to conducting ransomware incident investigations
You should make every effort to determine how the adversary gained access to your assets so that vulnerabilities can be remediated. Otherwise, the same type of attack will likely take place again in the future. In some cases,
the threat actor takes steps to cover their tracks and destroy evidence, so it is possible that the entire chain of events may not be evident.
The following are three key steps in DART ransomware investigations:
1. Assess the current situation Understand the scope
What initially made you aware of a ransomware attack?
What time/date did you first learn of the incident?
What logs are available and is there any indication that the actor is currently accessing systems?
Step 2: Identify which line-of-business (LOB) apps are unavailable due to a ransomware incident.
2. Identify the affected line-of-business (LOB) apps Get systems back online
Does the application require an identity?
Are backups of the application, configuration, and data available?
Are the content and integrity of backups regularly verified using a restore exercise?
Step 3: Identify the compromise recovery process.
3. Determine the compromise recovery (CR) process Remove attacker control from the environment
Question 5:
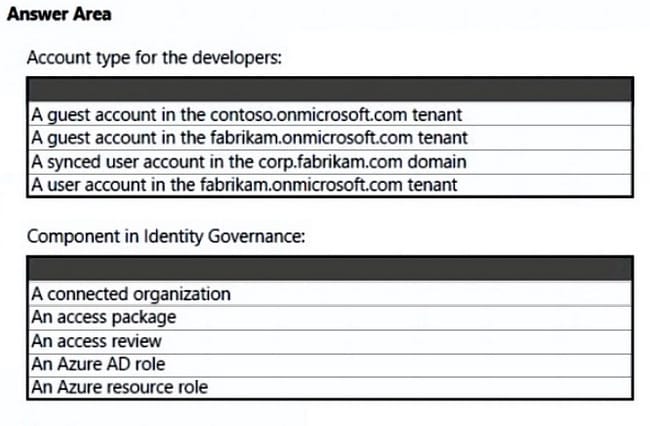
What should you create in Azure AD to meet the Contoso developer requirements?
Hot Area:
Correct Answer:
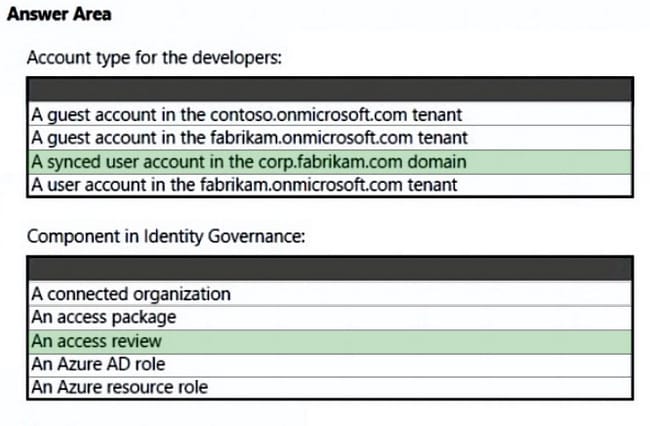
Box 1: A synced user account
Need to use a synched user account.
Incorrect:
*Not A user account in the fabrikam.onmicrosoft.com tenant
The Contoso developers must use their existing contoso.onmicrosoft.com credentials to access the resources in Sub1.
*Guest accounts would not meet the requirements.
Note: Developers at Contoso will connect to the resources of Fabrikam to test or update applications. The developers will be added to a security group named ContosoDevelopers in fabrikam.onmicrosoft.com that will be assigned to roles in
Sub1.
The ContosoDevelopers group is assigned the db_owner role for the ClaimsDB database.
Contoso Developers Requirements
Fabrikam identifies the following requirements for the Contoso developers:
Every month, the membership of the ContosoDevelopers group must be verified.
The Contoso developers must use their existing contoso.onmicrosoft.com credentials to access the resources in Sub1.
The Contoso developers must be prevented from viewing the data in a column named MedicalHistory in the ClaimDetails table.
Box 2: An access review
Scenario: Every month, the membership of the ContosoDevelopers group must be verified.
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User\’s access can be reviewed regularly to make sure only
the right people have continued access.
Access review is part of Azure AD Identity governance.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/synchronization
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Question 6:
HOTSPOT
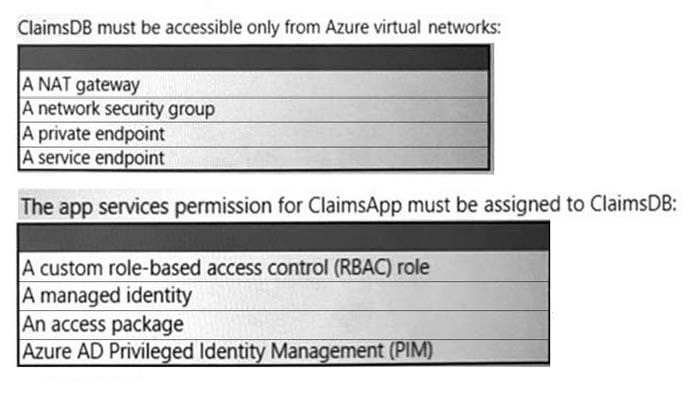
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
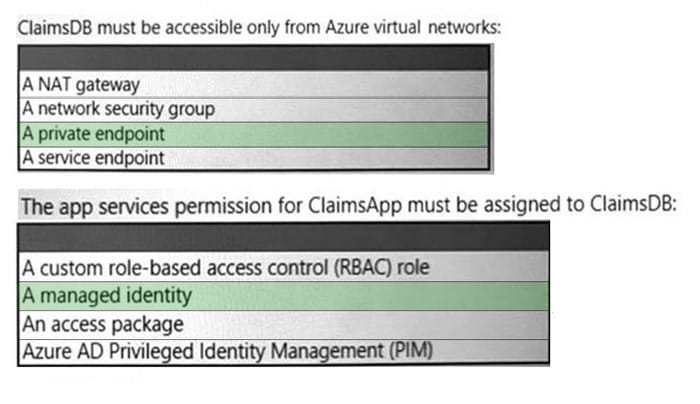
Box 1: A private endpoint Scenario: An Azure SQL database named ClaimsDB that contains a table named ClaimDetails
Requirements. ClaimsApp Deployment.
Fabrikam plans to implement an internet-accessible application named ClaimsApp that will have the following specifications:
1.ClaimsApp will be deployed to Azure App Service instances that connect to Vnet1 and Vnet2.
2. Users will connect to ClaimsApp by using the URL of https://claims.fabrikam.com.
3.ClaimsApp will access data in ClaimsDB.
4.ClaimsDB must be accessible only from Azure virtual networks.
5.The app services permission for ClaimsApp must be assigned to ClaimsDB.
Web app private connectivity to Azure SQL Database. Architecture: Workflow
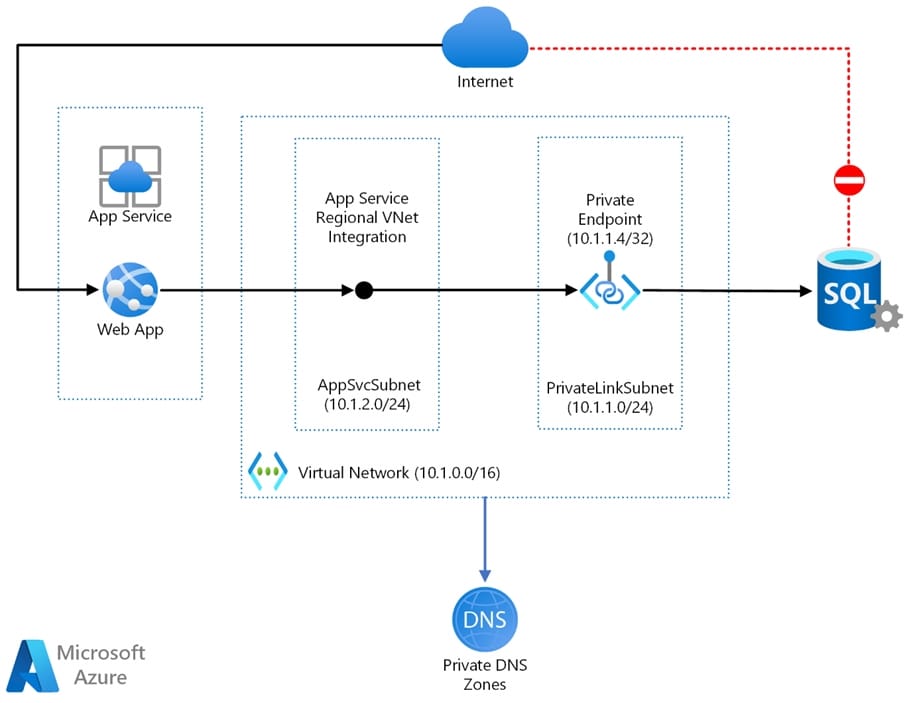
1. Using Azure App Service regional VNet Integration, the web app connects to Azure through an AppSvcSubnet delegated subnet in an Azure Virtual Network.
2. In this example, the Virtual Network only routes traffic and is otherwise empty, but other subnets and workloads could also run in the Virtual Network.
3. The App Service and Private Link subnets could be in separate peered Virtual Networks, for example as part of a hub-and-spoke network configuration.
4. Azure Private Link sets up a private endpoint for the Azure SQL Database in the PrivateLinkSubnet of the Virtual Network.
5.The web app connects to the SQL Database private endpoint through the PrivateLinkSubnet of the Virtual Network.
The database firewall allows only traffic coming from the PrivateLinkSubnet to connect, making the database inaccessible from the public internet.
Box 2: A managed identity Managed identities for Azure resources provide Azure services with an automatically managed identity in Azure Active Directory. Using a managed identity, you can authenticate to any service that supports Azure AD authentication without managing credentials.
Reference: https://docs.microsoft.com/en-us/azure/architecture/example-scenario/private-web-app/private-web-app https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/managed-identities-status
Question 7:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For blob containers in Azure Storage, you recommend encryption that uses customer-managed keys (CMKs).
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
We need to use customer-managed keys.
Azure Storage encryption for data at rest.
Azure Storage uses service-side encryption (SSE) to automatically encrypt your data when it is persisted to the cloud. Azure Storage encryption protects your data and helps you to meet your organizational security and compliance commitments.
Data in Azure Storage is encrypted and decrypted transparently using 256-bit AES encryption.
Data in a new storage account is encrypted with Microsoft-managed keys by default. You can continue to rely on Microsoft-managed keys for the encryption of your data, or you can manage encryption with your keys. If you choose to
manage encryption with your keys, you have two options. You can use either type of key management, or both:
*You can specify a customer-managed key to use for encrypting and decrypting data in Blob Storage and in Azure Files.
*You can specify a customer-provided key on Blob Storage operations. A client making a read-or-write request against Blob Storage can include an encryption key on the request for granular control over how blob data is encrypted and decrypted.
Note: Automated key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency. You can use a rotation policy to configure rotation for each key. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
This feature enables end-to-end zero-touch rotation for encryption at rest for Azure services with a customer-managed key (CMK) stored in Azure Key Vault. Please refer to specific Azure service documentation to see if the service covers end-to-end rotation.
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-service-encryption https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-key-rotation
Question 8:
DRAG DROP
You have a Microsoft 365 subscription.
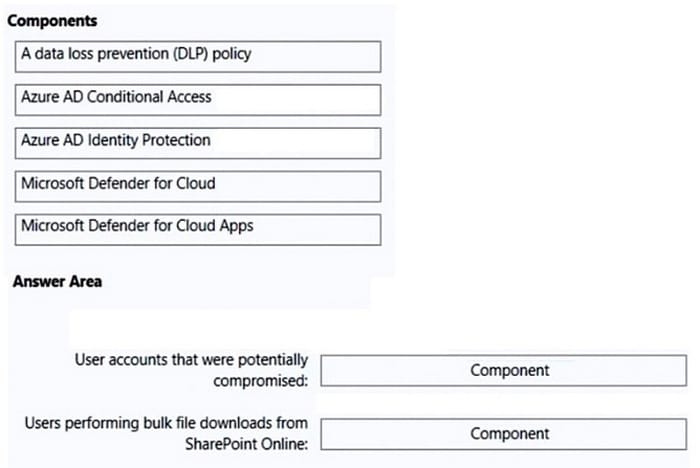
You need to recommend a security solution to monitor the following activities:
1.User accounts that were potentially compromised
2.Users performing bulk file downloads from Microsoft SharePoint Online
What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Correct Answer:
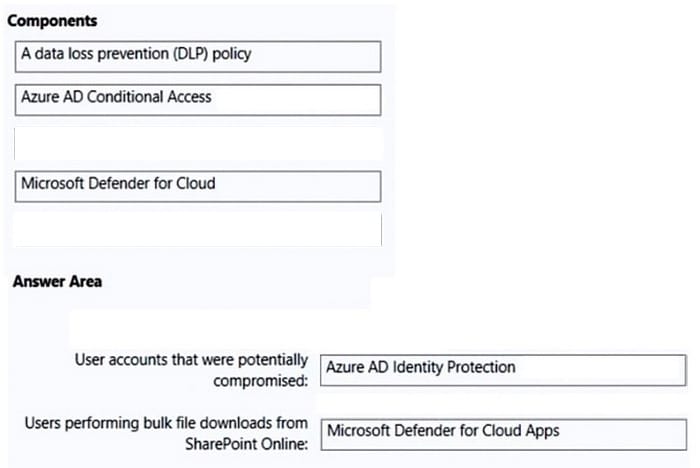
Box 1: Azure Active Directory (Azure AD) Identity Protection
Risk detections in Azure AD Identity Protection include any identified suspicious actions related to user accounts in the directory. Risk detections (both user and sign-in linked) contribute to the overall user risk score that is found in the Risky
Users report.
Identity Protection provides organizations access to powerful resources to see and respond quickly to these suspicious actions.
Note:
Premium sign-in risk detections include:
*Token Issuer Anomaly – This risk detection indicates the SAML token issuer for the associated SAML token is potentially compromised. The claims included in the token are unusual or match known attacker patterns.
*Suspicious inbox manipulation rules – This detection is discovered by Microsoft Defender for Cloud Apps. This detection profiles your environment and triggers alerts when suspicious rules that delete or move messages or folders are set on a user\’s inbox. This detection may indicate that the user\’s account is compromised, that messages are being intentionally hidden, and that the mailbox is being used to distribute spam or malware in your organization.
*Etc.
Incorrect:
Note: Microsoft 365 Defender for Cloud
Part of your incident investigation can include user accounts. You can see the details of user accounts identified in the alerts of an incident in the Microsoft 365 Defender portal from Incidents and alerts > Incident> Users.
Box 2: Microsoft 365 Defender for App
Defender for Cloud apps detect mass download (data exfiltration) policy
Detect when a certain user accesses or downloads a massive number of files in a short period.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks https://docs.microsoft.com/en-us/defender-cloud-apps/policies-threat-protection#detect-mass-download-data-exfiltration https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-users
Question 9:
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.
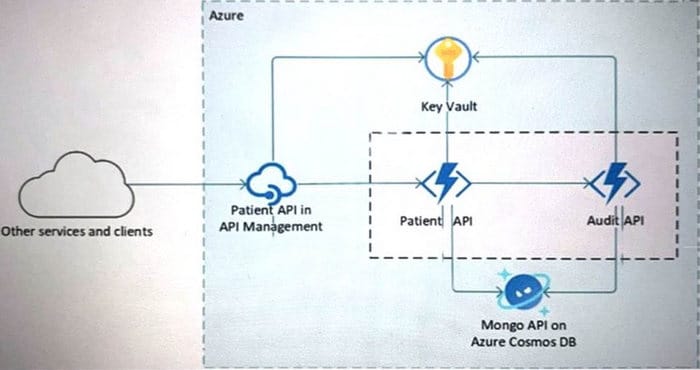
You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
A. Azure Active Directory (Azure AD) enterprise applications
B. an Azure App Service Environment (ASE)
C. Azure service endpoints
D. an Azure Active Directory (Azure AD) application proxy
Correct Answer: B
The Azure App Service Environment v2 is an Azure App Service feature that provides a fully isolated and dedicated environment for securely running App Service apps at a high scale. This capability can host you:
1.Windows web apps
2.Linux web apps
3.Docker containers
4.Mobile apps
5.Functions
App Service environments (ASEs) are appropriate for application workloads that require:
Very high scale.
Isolation and secure network access.
High memory utilization.
Customers can create multiple ASEs within a single Azure region or across multiple Azure regions. This flexibility makes ASEs ideal for horizontally scaling stateless application tiers in support of high requests per second (RPS) workloads.
Reference: https://docs.microsoft.com/en-us/azure/app-service/environment/intro
Question 10:
You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL).
You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment
What should you include during the application design phase?
A. static application security testing (SAST) by using SonarQube
B. dynamic application security testing (DAST) by using Veracode
C. threat modeling by using the Microsoft Threat Modeling Tool
D. software decomposition by using Microsoft Visual Studio Enterprise
Correct Answer: C
Threat modeling is a core element of the Microsoft Security Development Lifecycle (SDL). It\’s an engineering technique you can use to help you identify threats, attacks, vulnerabilities, and countermeasures that could affect your application.
You can use threat modeling to shape your application\’s design, meet your company\’s security objectives, and reduce risk.
Incorrect:
Not B: Advantages of Veracode\’s DAST test solution
With a black box test tool from Veracode, you can:
Simulate the actions of an actual attacker to discover vulnerabilities not found by other testing techniques.
Run tests on applications developed in any language – JAVA/JSP, PHP, and other engine-driven web applications.
Provide development and QA teams with a report on critical vulnerabilities along with information that lets them recreate the flaws.
Fix issues more quickly with detailed remediation information.
Develop long-term strategies for improving application security across your software portfolio using guidance and proactive recommendations from Veracode\’s expert.
Not D: SonarQube is a leading automatic code review tool to detect bugs, vulnerabilities and code smells in your code. Using Static Application Security Testing (SAST) you can do an analysis of vulnerabilities in your code, also known as
white-box testing to find about 50% of likely issues.
Reference: https://www.microsoft.com/en-us/securityengineering/sdl/threatmodeling
Question 11:
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
A. Apply read-only locks on the storage accounts.
B. Set the AllowSharcdKeyAccess property to false.
C. Set the AllowBlobPublicAcccss property to false.
D. Configure automated key rotation.
Correct Answer: A
A read-only lock on a storage account prevents users from listing the account keys. A POST request handles the Azure Storage List Keys operation to protect access to the account keys. The account keys provide complete access to data in
the storage account.
Incorrect:
Not A:
If any clients are currently accessing data in your storage account with Shared Key, then Microsoft recommends that you migrate those clients to Azure AD before disallowing Shared Key access to the storage account.
However, in this scenario, we cannot migrate to Azure AD due to the legacy applications.
Note: Shared Key
A shared key is a very long string. You can simply access Azure storage by using this long string. It\’s almost like a password. It \’s worse: this is a master password. It gives you all sorts of rights on the Azure storage account. You can
imagine why this isn’t my favorite mechanism for accessing Azure storage. What happens when this key is compromised? You don’t get an alert. Perhaps you can set up monitoring to see misuse of your Azure storage account. But it\’s still less
than an ideal situation. Alerts will tell you of damage after it has already occurred.
Not C: Data breaches caused by cloud misconfiguration have been seen for the past few years. One of the most common misconfigurations is granting public access to cloud storage services. Such data is often unprotected, making them to
be accessed without any authentication method. Microsoft recently introduced a new protection feature to help avoid public access to storage accounts. The feature introduces a new property named allowBlobPublicAccess.
Not D: Key rotation would improve security.
Automated key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency.
You can use a rotation policy to configure rotation for each key. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
This feature enables end-to-end zero-touch rotation for encryption at rest for Azure services with a customer-managed key (CMK) stored in Azure Key Vault.
Reference: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
https://docs.microsoft.com/en-us/azure/storage/common/shared-key-authorization-prevent
https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-key-rotation
Question 12:
You have a Microsoft 365 tenant.
Your company uses a third-party software as a service (SaaS) app named App1 that is integrated with an Azure AD tenant.
You need to design a security strategy to meet the following requirements:
•Users must be able to request access to App1 by using a self-service request.
•When users request access to App1, they must be prompted to provide additional information about their request.
•Every three months, managers must verify that the users still require access to App1. What should you include in the design?
A.Microsoft Entra Identity Governance
B.connected apps in Microsoft Defender for Cloud Apps
C.access policies in Microsoft Defender for Cloud Apps
D.Azure AD Application Proxy
Correct Answer: A
Question 13:
Your company wants to optimize using Microsoft Defender for Endpoint to protect its resources against ransomware based on Microsoft Security Best Practices.
You need to prepare a post-breach response plan for compromised computers based on the Microsoft Detection and Response Team (DART) approach in Microsoft Security Best Practices.
What should you include in the response plan?
A. controlled folder access
B. application isolation
C. memory scanning
D. machine isolation
E. user isolation
Correct Answer: D
Explanation:
If a ransomware attack is detected the affected entity should immediately activate its security incident response plan, which should include measures to isolate the infected computer systems in order to halt propagation of the attack.
Note: Isolate devices from the network
Depending on the severity of the attack and the sensitivity of the device, you might want to isolate the device from the network. This action can help prevent the attacker from controlling the compromised device and performing further activities
such as data exfiltration and lateral movement.
Reference:
Question 14:
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel.
You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk.
What should you include in the recommendation?
A. a Microsoft Sentinel data connector
B. Azure Event Hubs
C. a Microsoft Sentinel workbook
D. Azure Data Factory
Correct Answer: A
Microsoft Sentinel Add-On for Splunk allows Azure Log Analytics and Microsoft Sentinel users to ingest security logs from the Splunk platform using the Azure HTTP Data Collector API. Reference: https://splunkbase.splunk.com/app/5312/
Question 15:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses customer-managed keys (CMKs).
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
We need to use customer-managed keys.
Transparent data encryption (TDE) helps protect Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics against the threat of malicious offline activity by encrypting data at rest. It performs real-time encryption and
decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
In Azure, the default setting for TDE is that the Database Encryption Key (DEK) is protected by a built-in server certificate. The built-in server certificate is unique for each server and the encryption algorithm used is AES 256.
TDE protector is either a service-managed certificate (service-managed transparent data encryption) or an asymmetric key stored in Azure Key Vault (customer-managed transparent data encryption).
Note: Automated key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency. You can use a rotation policy to configure rotation for each key. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
This feature enables end-to-end zero-touch rotation for encryption at rest for Azure services with a customer-managed key (CMK) stored in Azure Key Vault. Please refer to specific Azure service documentation to see if the service covers end-to-end rotation.
Reference: https://docs.microsoft.com/en-us/azure/azure-sql/database/transparent-data-encryption-tde-overview
https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-key-rotation
The third step is to calm down
After the previous study, you have studied the SC-100 exam content and learning resources and practiced your skills. Now you just need to calm down and prepare for the exam. Mindset will also affect the success or failure of the exam, you don’t have to be anxious, believe in yourself, and after these careful preparations, the exam is okay.
SC-100 exam employment unit
Let’s imagine what companies you will be able to work for if you pass the SC-100 exam. After all, the ultimate goal of studying hard for exams is to find a better job and realize your value.
You may be working for one of these companies:
- IBM
- Verizon
- Akamai
- Cisco
- Intel Corporation
- Microsoft
- Amazon
- Accenture
- Oracle
- Check Point Software Technologies
- Honeywell
- Salesforce
- General Motors (GM)
- TEKsystems
- AT&T
- Bank of America
- Amazon Web Services
- Cognizant Technology Solutions
- Citi
- …
If you’d like to see how much each company pays for this role, check out the Glassdoor website.
Globally, according to Glassdoor, after completing the Microsoft Cybersecurity Architect certification, the United States has the highest salary level. This is a great opportunity for you to participate.
Final thoughts
Studying for the SC-100 exam is a lot.
Here you will learn how to study for the SC-100 examand about employment prospects after successfully passing the exam.
Here you can get the best study resources for the SC-100 exam, Pass4itSure SC-100 practice questions https://www.pass4itsure.com/sc-100.html (PDF+VCE) to help you study for the SC-100:Microsoft Cybersecurity Architect exam with ease. Good luck!