
When people first look at SC-401, the reaction is often the same:
“Isn’t this just labels and DLP policies?”
“It sounds straightforward—so why do so many candidates struggle?”
Those questions aren’t naïve. They’re honest.
MICROSOFT-TECHNET collects the latest Microsoft (Azure,Microsoft 365,Power Platform,windows,Graph…) exam questions from Pass4itsure Microsoft Exam Dumps | Updated throughout the year

When people first look at SC-401, the reaction is often the same:
“Isn’t this just labels and DLP policies?”
“It sounds straightforward—so why do so many candidates struggle?”
Those questions aren’t naïve. They’re honest.
How can the latest MB-820 practice questions help candidates prepare for the Microsoft Dynamics 365 Business Central Developer certification?
It helps candidates test their knowledge, get familiar with the exam format, identify weak areas, and review more effectively.
According to user feedback from Pass4itsure, the similarity rate isaround 90%.
» Read more about: Free Latest MB-820 practice questions to boost your prep »
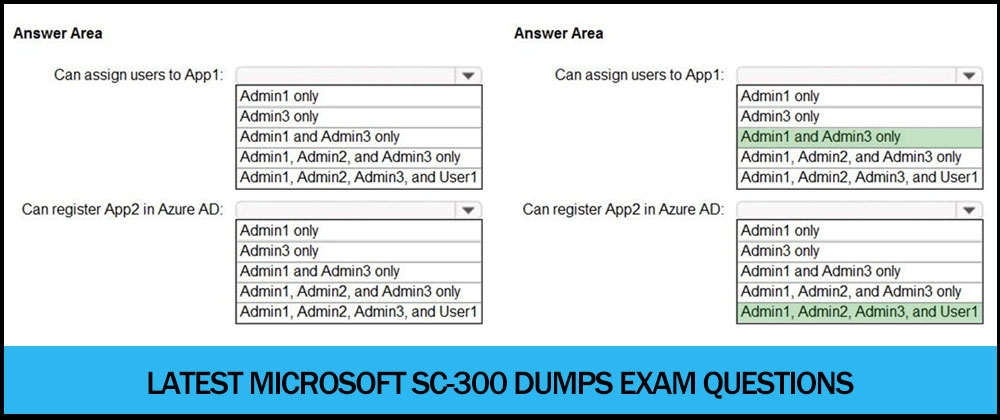
Microsoft SC-300 dumps are the exam materials that will help you pass the SC-300 certification exam successfully. They are the latest on the Internet! Download Microsoft SC-300 dumps: https://www.pass4itsure.com/sc-300.html, which contains 305 latest exam questions and answers to ensure you pass the exam successfully on your first attempt.
» Read more about: Share the latest Microsoft sc-300 dumps exam questions »
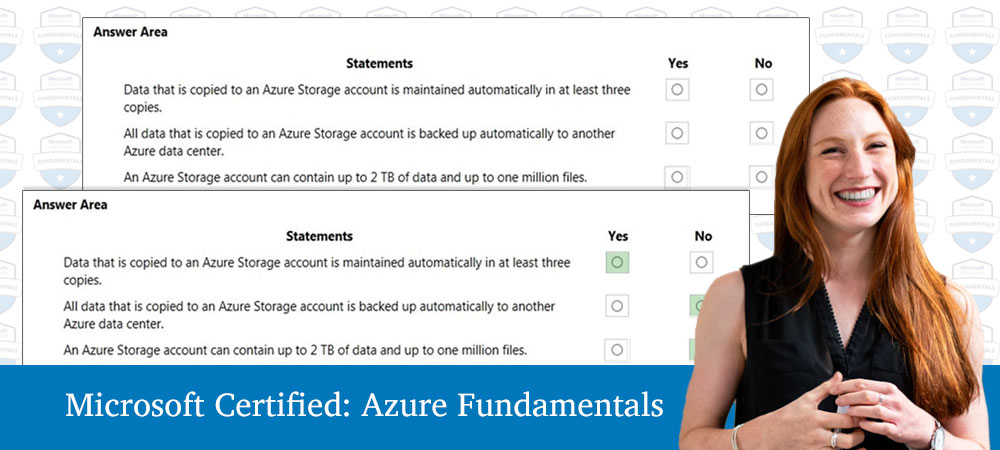
Our updated new AZ-900 exam dumps are a suitable study resource for Microsoft AZ-900 exams to help you pass the exam effectively.
New AZ-900 exam dumps are available online: https://www.pass4itsure.com/az-900.html brand new AZ-900 study resources that effectively help you prepare for the Microsoft Azure Fundamentals exam.
What does the Microsoft Azure Fundamentals Exam Looks Like?
A true AZ-900 test requires you to answer 40-60 questions in 45 minutes and score 700 to pass. Successfully pass the exam to earn Microsoft Azure Fundamentals certification.
» Read more about: AZ-900 Exam Dumps [New] | Helpful AZ-900 Study Resources »
Microsoft MB-820 dumps exam materials come with PDF and VCE exam practice methods. Both learning methods include 56 latest exam questions and answers!

Most importantly, download the latest Microsoft MB-820 dumps provided by Pass4itsure: https://www.pass4itsure.com/mb-820.html, which ensures candidates can successfully pass Microsoft Certified: Dynamics 365 Business Central Developer in one attempt Associate exam.
» Read more about: Latest Microsoft MB-820 dumps exam materials »

Learning Microsoft Fabric Analytics Engineer certification DP-600 exam requires complete guide, latest DP-600 exam resources and DP-600 exam dumps practice questions! You can go to download Pass4itSure DP-600 exam dumps practice questions https://www.pass4itsure.com/dp-600.html (pdf+vce) to practice effectively and improve your exam ability.
My purpose of writing this blog is to bring all DP-600 study resources in one place to guide you to prepare for the exam properly. I hope everyone preparing for this exam will find this blog useful and ultimately help you master all the skills you need to become a Certified Fabric AnalysisEngineer.
» Read more about: Complete Guide To DP-600 Microsoft Fabric Analytics Engineer Certification »

Suppose you want to take your place in today’s hot flow AI. In that case, you must mention the Microsoft Azure AI Fundamentals AI-900 exam, free Microsoft Azure AI Fundamentals AI-900 exam practice questions, and experience to help you easily pass the exam. In particular, Pass4itSure AI-900 exam practice questions resources (https://www.pass4itsure.com/ai-900.html) PDF+VCE mode is optional.
Contemporary, AI-900 exam breakthrough
In the current era of rapid development of AI, people face many challenges, but it is not impossible to break the situation and be reborn. Passing the AI-900 exam can earn the Microsoft Azure AI Fundamentals certification, and mastering the fundamentals of AI can help you in your career. The exam covers basic AI concepts, application scenarios, key technologies, and ethical principles, and applies to roles such as AI engineers, developers, data scientists, and students.

This article mainly shares the latest and free Azure AI Engineer Associate AI-102 exam questions (practice questions). It discusses how to pass the Azure AI (AI-102) exam in the current AI explosion.
Pass4itSure AI-102 Exam The latest practice questions https://www.pass4itsure.com/ai-102.html have been fully updated to help you prepare for the exam, embrace AI, and get your ticket to the times.

We are writing this blog post because many people have asked for information about the Microsoft Azure Data Engineer Associate Certification DP-203 exam how to study and the latest exam questions.
Pass4itSure’s new DP-203 exam questions (https://www.pass4itsure.com/dp-203.html) and an unwavering study plan will help you study for the exam correctly and pass it successfully.

This blog was created to help you confidently pass the Microsoft PL-600 exam, whether a veteran or a beginner. From the exam structure to how to pass, we’ve gathered the key information you need to succeed, including new exam practice questions (free of charge).
Let’s start with some important information!
Key information needed for success on the PL-600 exam:
Exam PL-600: Microsoft Power Platform Solution Architect
Topics covered and weighted in the PL-600 exam: Perform solution envisioning and requirement analysis (35–40%), Architect a solution (40–45%), Implement the solution (15–20%)
Passing score: 700
Number of exam questions: 40-60
Exam languages: English, French, German, Italian, Japanese, Portuguese (Brazilian), Spanish, Chinese (Simplified)
Exam duration: two hours
Examine: Perform solution vision and needs analysis; design solutions; and implement solutions.
» Read more about: Key Information PL-600 Exam And New Exam Practice Questions »