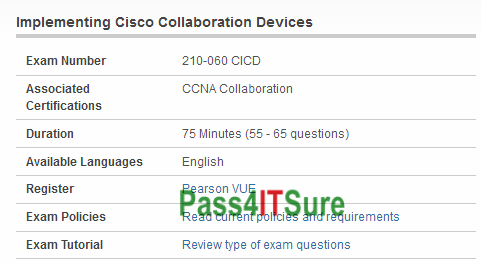
Which site offer Cisco 210-060 dumps practice test? Pass4itsure Cisco 210-060 exam questions materials are the shortcut to your success. The Implementing Cisco Collaboration Devices v1.0 (210-060 CICD) exam is a 75 Minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCNA Collaboration certification. Latest and updated Cisco 210-060 dumps exam questions and answers download and prepare 210-060 Youtube trainning now. “Implementing Cisco Collaboration Devices v1.0” is the exam name of Pass4itsure Cisco 210-060 dumps test which designed to help candidates prepare for and pass the Cisco 210-060 exam. The accuracy rate of Pass4itsure https://www.pass4itsure.com/210-060.html dumps test answers materials is high with wide coverage. It not only can improve your cultural knowledge, but also improve your operation level.
[2018-February-Version Pass4itsure 210-060 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNmlXYjFDT0t3UWc
[2018-February-Version Pass4itsure 210-065 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWQk1xeU5TZ3ExalE
Pass4itsure Cisco 210-060 Dumps Free Demo Download(34-61)
QUESTION 34
A voice engineer wants to monitor system activities using the RTMT tool. Which step is next after navigating to Cisco Unified Reporting?
A. system andgt; scheduler andgt; CDR
B. system reports andgt; unified CM data summary andgt; generate report
C. system andgt; tools andgt; reports
D. tools andgt; CDR analysis and reporting
210-060 exam Correct Answer: B
QUESTION 35
Which type of template should be used when a network engineer adds a new call center agent in the Cisco Unity Connection?
A. Contact
B. Call handler
C. User
D. Notification
Correct Answer: C
QUESTION 36
A single user receives a high amount of inbound voice messages and checks them only via email. The user cannot receive or send messages as the mailbox is full. Which option provides a permanent solution to this problem?
A. message aging policies
B. mailbox size quota
C. multiple mailbox stores
D. call-routing rules
E. restriction tables
210-060 dumps Correct Answer: A
QUESTION 37
Which CAR module report provides key information to determine if an additional gateway is needed?
A. gateway utilization
B. gateway summary
C. gateway detail
D. gateway and line group utilization
Correct Answer: A
QUESTION 38
Which IM and Presence chat feature allows for an always-available chat room that remains active, even if all of the participants leave the chat?
A. Personal
B. Group
C. Persistent
D. Ad-hoc
210-060 pdf Correct Answer: C
QUESTION 39
In which section of Cisco Unified Communications Manager are Call Detail Records viewed?
A. Cisco Unified Serviceability
B. Cisco Unified OS Administration
C. Cisco Unified Reporting
D. Cisco Unified Communications Manager Administration
E. Cisco Unified Disaster Recovery
Correct Answer: A
QUESTION 40
Which Cisco Unity Connection user field is used to map to an LDAP directory?
A. SMTP Address
B. Last Name
C. Alias
D. Display Name
210-060 vce Correct Answer: C
QUESTION 41
_______ is one of the programs used to wardial.
A. DialIT
B. Netstumbler
C. TooPac
D. Kismet
E. ToneLoc
Correct Answer: E
Explanation
Explanation/Reference:
Explanation:
ToneLoc is one of the programs used to wardial. While this is considered an “old school” technique, it is still effective at finding backdoors and out of band network entry points.
QUESTION 42
What are the default passwords used by SNMP?(Choose two.)
A. Password
B. SA
C. Private
D. Administrator
E. Public
F. Blank
210-060 exam Correct Answer: CE
Explanation
Explanation/Reference:
Explanation:
Besides the fact that it passes information in clear text, SNMP also uses well-known passwords. Public and private are the default passwords used by SNMP.
QUESTION 43
Which of the following ICMP message types are used for destinations unreachables?
A. 0
B. 3
C. 11
D. 13
E. 17
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Type 3 messages are used for unreachable messages. 0 is Echo Reply, 8 is Echo request, 11 is time exceeded, 13 is timestamp and 17 is subnet mask request. Learning these would be advisable for the test.
QUESTION 44
What is the proper response for a FIN scan if the port is closed?
A. SYN
B. ACK
C. FIN
D. PSH
E. RST
210-060 dumps Correct Answer: E
Explanation
Explanation/Reference:
Explanation:
Closed ports respond to a FIN scan with a RST.
QUESTION 45
What is the proper response for a FIN scan if the port is open?
A. SYN
B. ACK
C. FIN
D. PSH
E. RST
F. No response
Correct Answer: F
Explanation
Explanation/Reference:
Explanation:
Open ports respond to a FIN scan by ignoring the packet in question.
QUESTION 46
What is the proper response for a X-MAS scan if the port is closed?
A. SYN
B. ACK
C. FIN
D. PSH
E. RST
F. No response
210-060 pdf Correct Answer: E
Explanation
Explanation/Reference:
Explanation:
Closed ports respond to a X-MAS scan with a RST.
QUESTION 47
What is the proper response for a X-MAS scan if the port is open?
A. SYN
B. ACK
C. FIN
D. PSH
E. RST
F. No response
Correct Answer: F
Explanation
Explanation/Reference:
Explanation:
Closed ports respond to a X-MAS scan by ignoring the packet.
QUESTION 48
What flags are set in a X-MAS scan?(Choose all that apply.
A. SYN
B. ACK
C. FIN
D. PSH
E. RST
F. URG
210-060 vce Correct Answer: CDF
Explanation
Explanation/Reference:
Explanation:
FIN, URG, and PSH are set high in the TCP packet for a X-MAS scan
QUESTION 49
Which of the following is an automated vulnerability assessment tool.
A. Whack a Mole
B. Nmap
C. Nessus
D. Kismet
E. Jill32
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Nessus is a vulnerability assessment tool.
QUESTION 50
John is using a special tool on his Linux platform that has a signature database and is therefore able to detect hundred of vulnerabilities in UNIX, Windows, and commonly-used web CGI scripts. Additionally, the database detects DDoS zombies and Trojans. What would be the name of this multifunctional tool?
A. nmap
B. hping
C. nessus
D. make
210-060 exam Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Nessus is the world’s most popular vulnerability scanner, estimated to be used by over 75,000 organizations world-wide. Nmap is mostly used for scanning, not for detecting vulnerabilities. Hping is a free packet generator and analyzer for the TCP/IP protocol and make is used to automatically build large applications on the nix plattform.
QUESTION 51
________ is an automated vulnerability assessment tool.
A. Whack a Mole
B. Nmap
C. Nessus
D. Kismet
E. Jill32
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Nessus is a vulnerability assessment tool.
QUESTION 52
What is the disadvantage of an automated vulnerability assessment tool?
A. Ineffective
B. Slow
C. Prone to false positives
D. Prone to false negatives
E. Noisy
210-060 dumps Correct Answer: E
Explanation
Explanation/Reference:
Explanation:
Vulnerability assessment tools perform a good analysis of system vulnerabilities; however, they are noisy and will quickly trip IDS systems.
QUESTION 53
What are two things that are possible when scanning UDP ports? (Choose two.
A. A reset will be returned
B. An ICMP message will be returned
C. The four-way handshake will not be completed
D. An RFC 1294 message will be returned
E. Nothing
Correct Answer: BE
Explanation
Explanation/Reference:
Explanation:
Closed UDP ports can return an ICMP type 3 code 3 message. No response can mean the port is open or the packet was silently dropped.
QUESTION 54
Which of the following ICMP message types are used for destinations unreachables?
A. 0
B. 3
C. 11
D. 13
E. 17
210-060 pdf Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Type 3 messages are used for unreachable messages. 0 is Echo Reply, 8 is Echo request, 11 is time exceeded, 13 is timestamp and 17 is subnet mask request. Learning these would be advisable for the test.
QUESTION 55
What does a type 3 code 13 represent?(Choose two.
A. Echo request
B. Destination unreachable
C. Network unreachable
D. Administratively prohibited
E. Port unreachable
F. Time exceeded
Correct Answer: BD
Explanation
Explanation/Reference:
Explanation:
Type 3 code 13 is destination unreachable administratively prohibited. This type of message is typically returned from a device blocking a port.
QUESTION 56
Destination unreachable administratively prohibited messages can inform the hacker to what?
A. That a circuit level proxy has been installed and is filtering traffic
B. That his/her scans are being blocked by a honeypot or jail
C. That the packets are being malformed by the scanning software
D. That a router or other packet-filtering device is blocking traffic
E. That the network is functioning normally
210-060 vce Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Destination unreachable administratively prohibited messages are a good way to discover that a router or other low-level packet device is filtering traffic. Analysis of the ICMP message will reveal the IP address of the blocking device and the filtered port. This further adds the to the network map and information being discovered about the network and hosts.
QUESTION 57
Which of the following Nmap commands would be used to perform a stack fingerprinting?
A. Nmap -O -p80 <host(s.>
B. Nmap -hU -Q<host(s.>
C. Nmap -sT -p <host(s.>
D. Nmap -u -o -w2 <host>
E. Nmap -sS -0p target
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
This option activates remote host identification via TCP/IP fingerprinting. In other words, it uses a bunch of techniques to detect subtlety in the underlying operating system network stack of the computers you are scanning. It uses this information to create a “fingerprint” which it compares with its database of known OS fingerprints (the nmap-os-fingerprints file. to decide what type of system you are scanning.
QUESTION 58
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.) Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal? What is odd about this attack? Choose the best answer.
A. This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
B. This is back orifice activity as the scan comes form port 31337.
C. The attacker wants to avoid creating a sub-carries connection that is not normally valid.
D. These packets were crafted by a tool, they were not created by a standard IP stack.
210-060 exam Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Port 31337 is normally used by Back Orifice. Note that 31337 is hackers spelling of `elite’, meaning `elite hackers’.
QUESTION 59
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
A. SYN scan
B. ACK scan
C. RST scan
D. Connect scan
E. FIN scan
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
The TCP full connect (-sT) scan is the most reliable.
QUESTION 60
Name two software tools used for OS guessing.(Choose two.
A. Nmap
B. Snadboy
C. Queso
D. UserInfo
E. NetBus
210-060 dumps Correct Answer: AC
Explanation
Explanation/Reference:
Explanation:
Nmap and Queso are the two best-known OS guessing programs. OS guessing software has the ability to look at peculiarities in the way that each vendor implements the RFC’s. These differences are compared with its database of known OS fingerprints. Then a best guess of the OS is provided to the user.
QUESTION 61
Sandra is the security administrator of ABC.com. One day she notices that the ABC.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately. Which organization coordinates computer crime investigations throughout the United States?
A. NDCA
B. NICP
C. CIRP
D. NPC
E. CIA
Correct Answer: D
Explanation
Explanation/Reference:

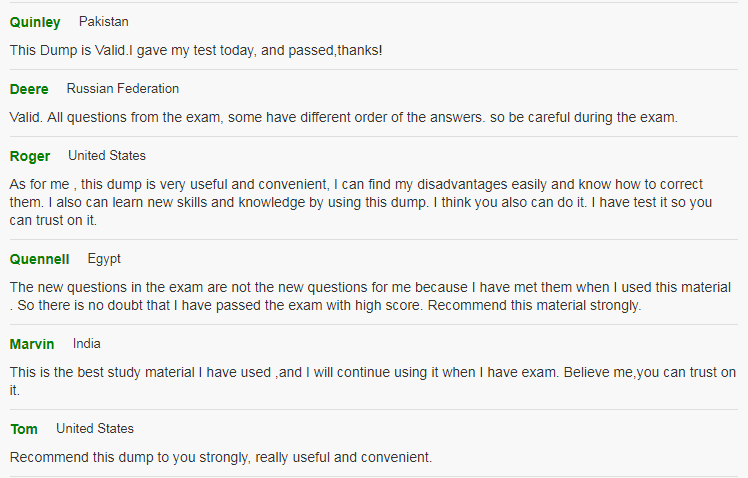
See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products.Our Cisco 210-060 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
Pass4itsure Cisco 210-060 dumps exam questions have an advantage over any other exam dumps.”Implementing Cisco Collaboration Devices v1.0″, also known as 210-060 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Because this is the exam dumps that can help you pass 210-060 exam questions at the first attempt. Pass4itsure Cisco 210-060 dumps exam questions answers are updated (203 Q&As) are verified by experts. High passing rate of Pass4itsure questions and answers is certified by many more candidates. The associated certifications of 210-060 dumps is CCNA Collaboration. With the exam dumps, you can not only save a lot of time in the process of preparing for https://www.pass4itsure.com/210-060.html dumps exam questions, also can get high marks in the exam.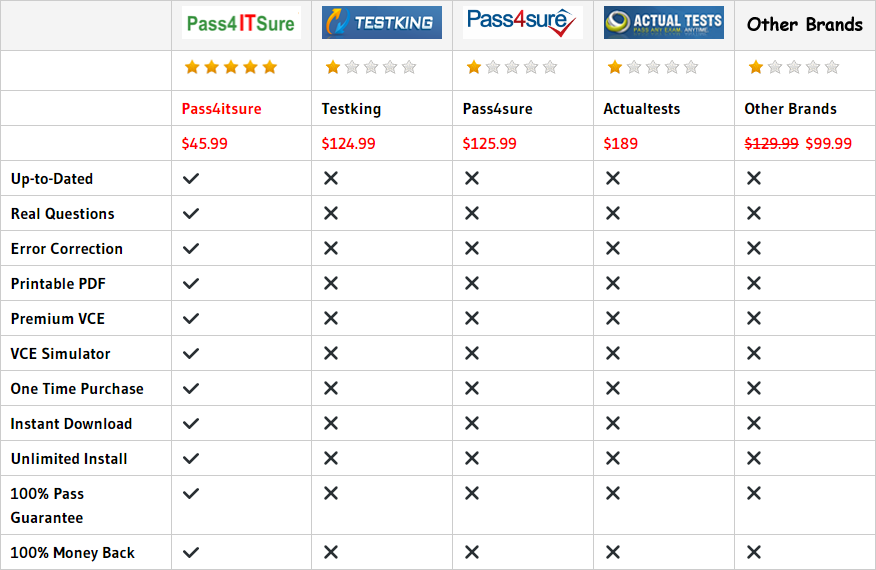
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloadable, error correction, unlimited install,etc. Such as Pass4itsure Latest Upload Cisco 210-060 Dumps Exam Questions And Answers, Real Cisco 210-060 Dumps Certification Material, We Help You Pass Implementing Cisco Collaboration Devices v1.0. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!