Pass4itSure Microsoft 98-367 exam dumps are designed with the help of Microsoft’s real exam content. You can get 98-367 VCE dumps and 98-367 PDF dumps from Pass4itSure! Check out the best and updated 98-367 exam questions by Pass4itSure 98-367 dumps https://www.pass4itsure.com/98-367.html (Q&As: 277) (VCE and PDF), we are very confident that you will be successful on Microsoft 98-367 exam.
Microsoft 98-367 exam questions in PDF file
Download those Pass4itSure 98-367 pdf from Google Drive: https://drive.google.com/file/d/13KEkSa7iZUYzvdT6W_H2JOXaWd4u5Sl7/view?usp=sharing
Microsoft MTA Certifications:
98-349 :Windows Operating System Fundamentals
98-349 practice test free https://www.microsoft-technet.com/get-pass4itsure-microsoft-98-349-exam-dumps-as-practice-test-and-pdf.html
Following are some Microsoft 98-367 exam questions for review (Microsoft 98-367 practice test 1-13)
QUESTION 1
You have a Windows 2012 R2 Server. Security logging is enabled. You use this log for several audits of the server.
You need to make sure the log is not overwritten when it reaches its maximum log size.
What should you do?
A. Copy logs regularly to a different location
B. Maintain a backup of the log file
C. Increase the log file size
D. Enable archiving
Correct Answer: D
QUESTION 2
The company that you work for wants to set up a secure network, but they do not have any servers. Which three
security methods require the use of a server? (Choose three.)
A. 802.1x
B. WPA2 Personal
C. WPA2 Enterprise
D. RADIUS
E. 802.11ac
Correct Answer: ACD
QUESTION 3
A group of users has access to Folder A and all of its contents. You need to prevent some of the users from accessing a
subfolder inside Folder A.
What should you do first?
A. Disable folder sharing
B. Hide the folder
C. Change the owner
D. Block inheritance
Correct Answer: A
QUESTION 4
Which of the following points has to be considered for using the BitLocker?
A. The deployment of antivirus because BitLocker needs a a removal of buffer overflow.
B. The deployment of SEAL because BitLocker needs an alternative encryption algorithm to software- based DES,
3DES, and AES. .
C. The deployment of hardware because BitLocker needs a system reserved partition.
D. The deployment of hard disk because BitLocker needs a bot.
Correct Answer: C
Answer: B is incorrect. SEAL is an alternative encryption algorithm to software- based DES, 3DES, and AES. It uses a
160-bit encryption key. SEAL provides less impact to the CPU than other software- based encryption algorithms. In
Cisco IOS IPSec implementations, SEAL supports the SEAL algorithm. It can be configured through the command-line
interface using the crypto ipsec transform-set command and the esp-seal transform option. Answer: A is incorrect.
Buffer overflow is a condition in which an application receives more data than it is configured to accept. It helps an
attacker not only to execute a malicious code on the target system but also to install backdoors on the target system for
further attacks. All buffer overflow attacks are due to only sloppy programming or poor memory management by the
application developers. The main types of buffer overflows are: Stack overflow Format string overflow Heap overflow
Integer overflow Answer: D is incorrect. A bot is defined as a program that is used to perform some task on a network
especially a task that is repetitive or time-consuming such as spybot or tracking software that uses other forms of
deceptive software and programs conducting some activities on a computer without getting appropriate consent from
the users.
QUESTION 5
You are preparing an audit policy for the workstations at Contoso, Ltd. Currently, no advanced auditing is enabled. The
workstations are not members of the domain. The settings of your Advanced Audit Policy Configuration are shown in the
following image:
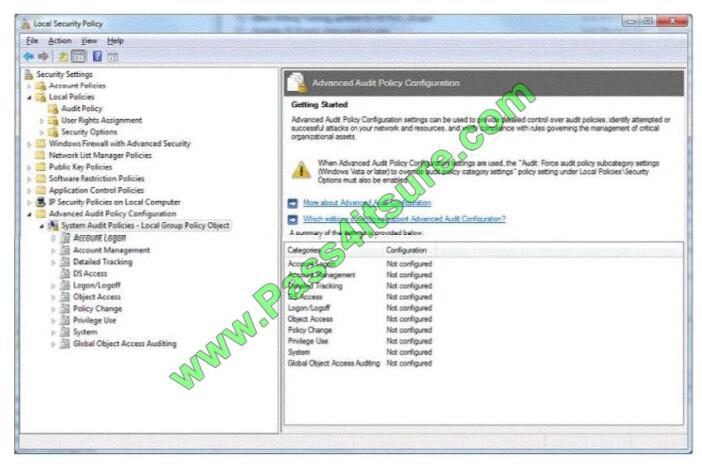
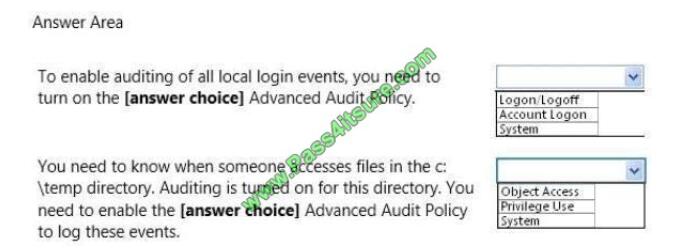
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth
one point.
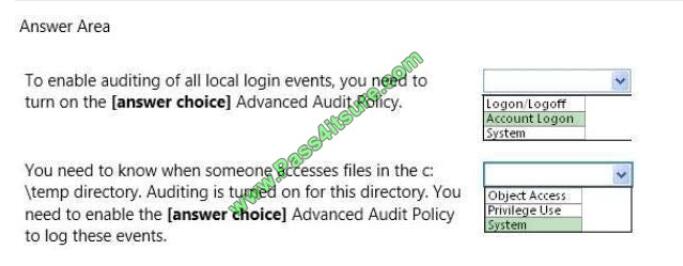
Hot Area:
Correct Answer:
QUESTION 6
The purpose of User Account Control (UAC) is to:
A. Encrypt the user\\’s account
B. Limit the privileges of software
C. Secure your data from corruption
D. Facilitate Internet filtering
Correct Answer: B
User Account Control (UAC) is a technology and security infrastructure introduced with Microsoft\\’s Windows machines.
It aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an
administrator authorizes an increase or elevation. In this way, only applications trusted by the user may receive
administrative privileges, and malware should be kept from compromising the operating system.
QUESTION 7
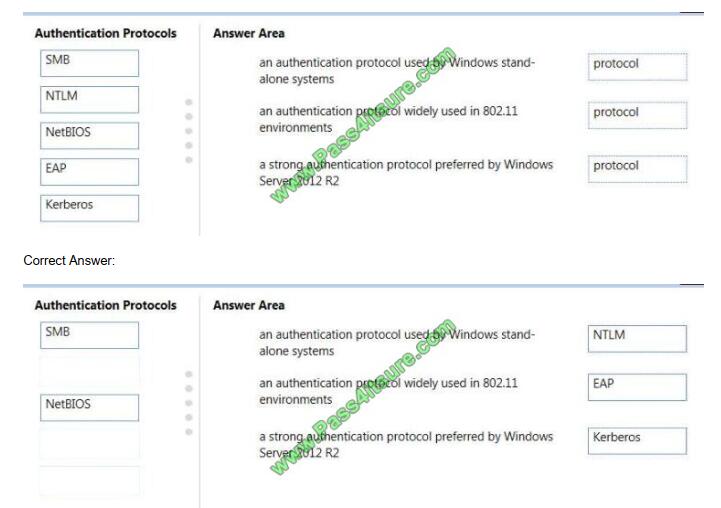
Match the authentication protocol with its description.
Instructions: To answer, drag the appropriate authentication protocol from the column on the left to its description on the
right. Each authentication protocol may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
QUESTION 8
This question requires that you evaluate the underlined text to determine if it is correct. The first line of defense against
attacks from the Internet is a software firewall.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed\\’\\’ if
the underlined text makes the statement correct.
A. hardware firewall
B. virus software
C. radius server
D. No change is needed
Correct Answer: A
QUESTION 9
You manage 50 Windows workstations in a computer lab. All workstations belong to the lab Active Directory domain.
You need to implement several audit policies on each workstation in the shortest time possible.
What should you do?
A. Enable logging on each computer
B. Create a domain Group Policy
C. Turn on the Audit Policy on the domain controller
D. Enable Audit object access
Correct Answer: B
References:
https://docs.microsoft.com/en-us/windows-server/networking/branchcache/deploy/use-group-policy-to-configure-domainmember-client-computers
QUESTION 10
Bridging is a process of sending packets from source to destination on OSI layer 3.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if
the underlined text makes the statement correct.
A. Routing
B. Switching
C. Repeating
D. No change is needed.
Correct Answer: A
QUESTION 11
You want to prevent external users from acquiring information about your network. You should implement a:
A. router
B. layer-3 switch
C. firewall
D. proxy server
Correct Answer: C
QUESTION 12
The certificate of a secure public Web server on the Internet should be:
A. Issued by a public certificate authority (CA)
B. Signed by using a 4096-bit key
C. Signed by using a 1024-bit key
D. Issued by an enterprise certificate authority (CA)
Correct Answer: A
QUESTION 13
Which of the following are required to enable for preventing the users from downloading and installing software from the
Internet? Each correct answer represents a complete solution. Choose all that apply.
A. Software restriction policies
B. PTR record
C. User Account Control
D. Anti-Virus software
Correct Answer: AC
Answer: C and A
It is required to enable User Account Control on all Windows 7 computers and to configure software restriction policies
to prevent the users from downloading and installing software from the Internet.
PS.
Thanks for reading! Hope the newest 98-367 exam dumps can help you in your exam. Get full 98-367 exam questions try Pass4itSure 98-367 dumps! 98-367 dumps in VCE and PDF are here: https://www.pass4itsure.com/98-367.html (Updated: Jun 18, 2021).
Download Pass4itSure 98-367 dumps pdf from Google Drive: https://drive.google.com/file/d/13KEkSa7iZUYzvdT6W_H2JOXaWd4u5Sl7/view?usp=sharing (98-367 Exam Questions)