How to get the Cisco exam 210-250 dumps with answers? It is recognized that the Understanding Cisco Cybersecurity Fundamentals 210-250 exam questions will be the hot test associated with pass4itsure https://www.pass4itsure.com/210-250.html dumps practice exam qualification. Pass4itsure is offering valid dumps for SECFND 210-250 dumps for your instant preparation. We provide you with the entire 109Q&A from the Cisco CCNA Cyber Ops study guide.
This could be the evaluation on the perfect combination and it will help you to pass 210-250 Understanding Cisco Cybersecurity Fundamentals study guide from initially cybersecurity’s basic principles, foundational knowledge, and core skills needed to grasp the more advanced associate-level materials in the second required exam, “Implementing Cisco Cybersecurity Operations (SECOPS)”. Pass4itsure CCNA Cyber Ops 210-250 dumps sample questions are available at the end of each chapter. The Cisco CCNA Cyber Ops certification covers the Cisco video Understanding Cisco Cybersecurity Fundamentals topics. Our 210-250 training material about the SECFND 210-250 exam that are helpful for quick revision.
- Instant Download After Purchase
- 100% Money Back Guarantee
- 365 Days Free Update
- 7000+ Satisfied Customer
Download Complete List of Topics in PDF format
1.0 Network Concepts 12%
- 1.1 Describe the function of the network layers as specified by the OSI and the TCP/IP network models
- 1.2 Describe the operation of the following
- 1.3 Describe the operation of these network services
- 1.4 Describe the basic operation of these network device types
- 1.5 Describe the functions of these network security systems as deployed on the host, network, or the cloud
- 1.6 Describe IP subnets and communication within an IP subnet and between IP subnets
- 1.7 Describe the relationship between VLANs and data visibility
- 1.8 Describe the operation of ACLs applied as packet filters on the interfaces of network devices
- 1.9 Compare and contrast deep packet inspection with packet filtering and stateful firewall operation
- 1.10 Compare and contrast inline traffic interrogation and taps or traffic mirroring
- 1.11 Compare and contrast the characteristics of data obtained from taps or traffic mirroring and NetFlow in the analysis of network traffic
- 1.12 Identify potential data loss from provided traffic profiles
2.0 Security Concepts 17%
- 2.1 Describe the principles of the defense in depth strategy
- 2.2 Compare and contrast these concepts
- 2.3 Describe these terms
- 2.4 Describe these security terms
- 2.5 Compare and contrast these access control models
- 2.6 Compare and contrast these terms
- 2.7 Describe these concepts
3.0 Cryptography 12%
- 3.1 Describe the uses of a hash algorithm
- 3.2 Describe the uses of encryption algorithms
- 3.3 Compare and contrast symmetric and asymmetric encryption algorithms
- 3.4 Describe the processes of digital signature creation and verification
- 3.5 Describe the operation of a PKI
- 3.6 Describe the security impact of these commonly used hash algorithms
- 3.7 Describe the security impact of these commonly used encryption algorithms and secure communications protocols
- 3.8 Describe how the success or failure of a cryptographic exchange impacts security investigation
- 3.9 Describe these items in regards to SSL/TLS
4.0 Host-Based Analysis 19%
- 4.1 Define these terms as they pertain to Microsoft Windows
- 4.2 Define these terms as they pertain to Linux
- 4.3 Describe the functionality of these endpoint technologies in regards to security monitoring
- 4.4 Interpret these operating system log data to identify an event
5.0 Security Monitoring 19%
- 5.1 Identify the types of data provided by these technologies
- 5.2 Describe these types of data used in security monitoring
- 5.3 Describe these concepts as they relate to security monitoring
- 5.4 Describe these NextGen IPS event types
- 5.5 Describe the function of these protocols in the context of security monitoring
6.0 Attack Methods 21%
- 6.1 Compare and contrast an attack surface and vulnerability
- 6.2 Describe these network attacks
- 6.3 Describe these web application attacks
- 6.4 Describe these attacks
- 6.5 Describe these endpoint-based attacks
- 6.6 Describe these evasion methods
- 6.7 Define privilege escalation
- 6.8 Compare and contrast remote exploit and a local exploit
What if I don’t pass the exam? How do I claim Refund?
Getting online help for prepared CCNA Cyber Ops 210-250 vce test is quite common these days. Any Pass4itsure.com user who fails the corresponding exam has 30 days from the date of purchase of Exam on Pass4itsure.com for a full refund. The Cisco 210-250 dumps simulator and 210-250 exam dumps are easily available at their professional site. We can accept and arrange a full refund requests only if your score report or any relevant filed be confirmed.
Pass4itsure Cisco 210-250 Dumps Free Demo Download(1-19)
Exam B
QUESTION 1
Which two protocols are used for email (Choose two )
A. NTP
B. DNS
C. HTTP
D. IMAP
E. SMTP
210-250 exam Correct Answer: DE
Explanation
QUESTION 2
At which OSI layer does a router typically operate?
A. Transport
B. Network
C. Data link
D. Application
Correct Answer: B
Explanation
QUESTION 3
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header, Which option is making this behavior possible?
A. TOR
B. NAT
C. encapsulation
D. tunneling
210-250 dumps Correct Answer: B
Explanation
QUESTION 4
Which option is a purpose of port scanning?
A. Identify the Internet Protocol of the target system.
B. Determine if the network is up or down
C. Identify which ports and services are open on the target host.
D. Identify legitimate users of a system.
Correct Answer: C
Explanation
QUESTION 5
An intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources. Which evasion technique does this attempt indicate?
A. traffic fragmentation
B. resource exhaustion
C. timing attack
D. tunneling
210-250 pdf Correct Answer: B
Explanation
QUESTION 6
Which two activities are examples of social engineering? (Choose two)
A. receiving call from the IT department asking you to verify your username/password to maintain the account
B. receiving an invite to your department’s weekly WebEx meeting
C. sending a verbal request to an administrator to change the password to the account of a user the administrator does know
D. receiving an email from MR requesting that you visit the secure HR website and update your contract information
E. receiving an unexpected email from an unknown person with an uncharacteristic attachment from someone in the same company
Correct Answer: AC
Explanation
QUESTION 7
Cisco pxGrid has a unified framework with an open API designed in a hub-and-spoke architecture. pxGrid is used to enable the sharing of contextual-based information from which devices?
A. From a Cisco ASA to the Cisco OpenDNS service
B. From a Cisco ASA to the Cisco WSA
C. From a Cisco ASA to the Cisco FMC
D. From a Cisco ISE session directory to other policy network systems, such as Cisco IOS devices and the Cisco ASA
210-250 vce Correct Answer: D
Explanation
Explanation/Reference:
QUESTION 8
Which definition of a daemon on Linux is true?
A. error check right after the call to fork a process
B. new process created by duplicating the calling process
C. program that runs unobtrusively in the background
D. set of basic CPU instructions
Correct Answer: C
Explanation
QUESTION 9
A user reports difficulties accessing certain external web pages, When examining traffic to and from the external domain in full packet captures, you notice many SYNs that have the same sequence number, source, and destination IP address, but have different payloads. Which problem is a possible explanation of this situation?
A. insufficient network resources
B. failure of full packet capture solution
C. misconfiguration of web filter
D. TCP injection
210-250 exam Correct Answer: D
Explanation
Explanation/Reference:
QUESTION 10
Which definition describes the main purpose of a Security Information and Event Management solution ?
A. a database that collects and categorizes indicators of compromise to evaluate and search for potential security threats
B. a monitoring interface that manages firewall access control lists for duplicate firewall filtering
C. a relay server or device that collects then forwards event logs to another log collection device
D. a security product that collects, normalizes, and correlates event log data to provide holistic views of the security posture
Correct Answer: D
Explanation
QUESTION 11
Which information security property is supported by encryption?
A. sustainability
B. integrity
C. confidentiality
D. availability
210-250 dumps Correct Answer: C
Explanation
QUESTION 12
Which term describes the act of a user, without authority or permission, obtaining rights on a system, beyond what were assigned?
A. authentication tunneling
B. administrative abuse
C. rights exploitation
D. privilege escalation
Correct Answer: D
Explanation
QUESTION 13
Which definition of the IIS Log Parser tool is true?
A. a logging module for IIS that allows you to log to a database
B. a data source control to connect to your data source
C. a powerful, versatile tool that makes it possible to run SQL-like queries against log flies
D. a powerful versatile tool that verifies the integrity of the log files
210-250 pdf Correct Answer: C
Explanation
QUESTION 14
What are the advantages of a full-duplex transmission mode compared to half-duplex mode? (Select all that apply.)
A. Each station can transmit and receive at the same time.
B. It avoids collisions.
C. It makes use of backoff time.
D. It uses a collision avoidance algorithm to transmit.
Correct Answer: AB
Explanation
Explanation/Reference:
QUESTION 15
Which term represents the chronological record of how evidence was collected- analyzed, preserved, and transferred?
A. chain of evidence
B. evidence chronology
C. chain of custody
D. record of safekeeping
210-250 vce Correct Answer: C
Explanation
QUESTION 16
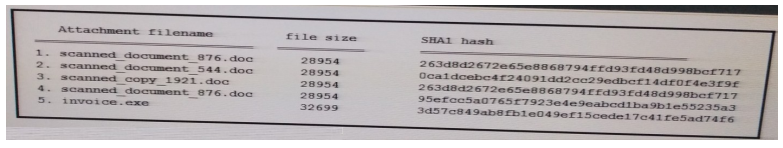
Refer to the exhibit. During an analysis this list of email attachments is found. Which files contain the same content?
A. 1 and 4
B. 3 and 4
C. 1 and 3
D. 1 and 2
Correct Answer: C
Explanation
QUESTION 17
In which case should an employee return his laptop to the organization?
A. When moving to a different role
B. Upon termination of the employment
C. As described in the asset return policy
D. When the laptop is end of lease
210-250 exam Correct Answer: C
Explanation
QUESTION 18
A firewall requires deep packet inspection to evaluate which layer?
A. application
B. Internet
C. link
D. transport
Correct Answer: A
Explanation
QUESTION 19
Which event occurs when a signature-based IDS encounters network traffic that triggers an alert?
A. connection event
B. endpoint event
C. NetFlow event
D. intrusion event
210-250 dumps Correct Answer: D
Explanation
Do you maintain 100% Guarantee on Pass4itsure.com products?
For your ease in 210-250 practice test we have also prepared comprehensive questions that are in pdf files. Yes. Our PDF of 210-250 exam is designed to ensure everything which you need to pass your exam successfully. At pass4itsure.com, we have a completely customer oriented policy. We invite the rich experience and expert knowledge of professionals from the IT certification industry to guarantee the PDF details precisely and logically. After the end of your preparation you can use them. Our customers’ time is a precious concern for us. This requires us to provide you the products that can be utilized most efficiently. They contain all the 210-250 dumps questions in summarized form.
Pass4itsure’s training materials can test your knowledge in preparing for the exam, and can evaluate your performance within a fixed time. A lot of companies are offering cheap 210-250 dumps for Understanding Cisco Cybersecurity Fundamentals exam but with little to no good results. The instructions given to you for your weak link, so that you can prepare for the exam better. This exam is specially linked with Cisco CCNA Cyber Ops certification. Pass4itsure 210-250 dumps is consists of different types of multiple choice questions and answers. The pass4itsure’s Cisco 300-365 New Practice Questions Download exam training materials introduce you many themes that have different logic. So that you can learn the various technologies and subjects.
Learning Resources
Self-Study E-Learning
- Understanding Cisco Cybersecurity Fundamentals (SECFND) v1.0
Instructor Led Training
- Understanding Cisco Cybersecurity Fundamentals (SECFND) v1.0
[2018-May-Version Pass4itsure Cisco 210-250 PDF Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWRzdFOXJORHhsck0
[2018-May-Version Pass4itsure Cisco 200-150 PDF Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWTi1YUDlKM3U3R1U
We guarantee that our training materials has tested through the practice. Many candidates may spend a lot of time on this exam; some candidates may even feel depressed after twice or more failure. pass4itsure have done enough to prepare for your exam. Right now you may need our pass4itsure 210-250 dumps exams (someone also calls 070-489 exam cram). Our material is comprehensive, and the price is reasonable. You have found the right place to guide you with the best that is in the industry to pass your desired exam. Here, candidates can get Cisco 210-250 questions answers that are prepared by the expert faculty.
This study guide is designed as per Cisco – Understanding Cisco Cybersecurity Fundamentals test engine with free 210-250 dumps. There are few exams like Cisco 210-250 dumps that will help you in your career boost. Once you choose our 210-250 dumps pdf study guide with pass4itsure, we provide one-year updating service of test questions in accordance with the latest test trend, you can save your time of searching them by yourself. It needs extreme expert choice along with great proficiency.
Pass4itsure Cisco 210-250 Dumps PDF, Buy Best Cisco 210-250 Dumps Online, We Help You Pass Understanding Cisco Cybersecurity Fundamentals.
Pass4itsure Promo Code 15% Off